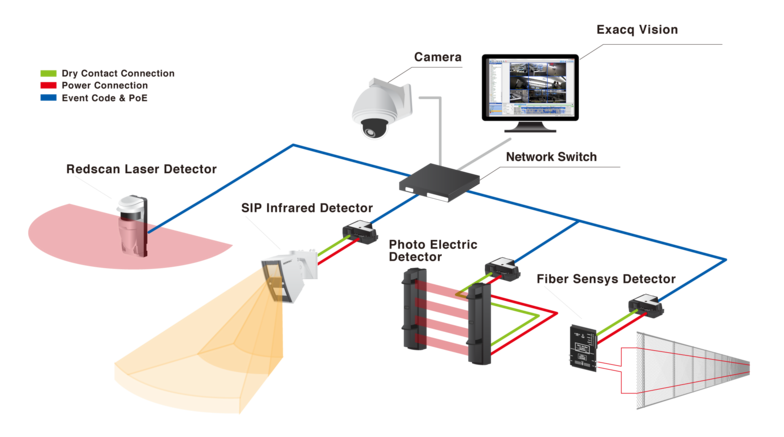
Optex IP sensors and detectors communicate through a network using UDP or TCP. Incoming code events from a Optex detector/sensor into Exacq Vision can trigger custom actions as well as send a command to move a PTZ camera to a selected preset.
Click Here for Redscan setup support materials
Click Here for PIE-1 setup support materials (Required for Redwall SIP and RedBeam Photoelectric Detectors)
**Must be certified to install Optex IP Detectors
See how you can maximize the value of VMS with Optex IP detectors
Increase the value of Exacq Vision Video Management Software and IP Video Surveillance
Integrating Optex IP sensors and detectors with your Video Management Software increases the effectiveness of video detection and surveillance applications by addressing common problems associated with video driven solutions.
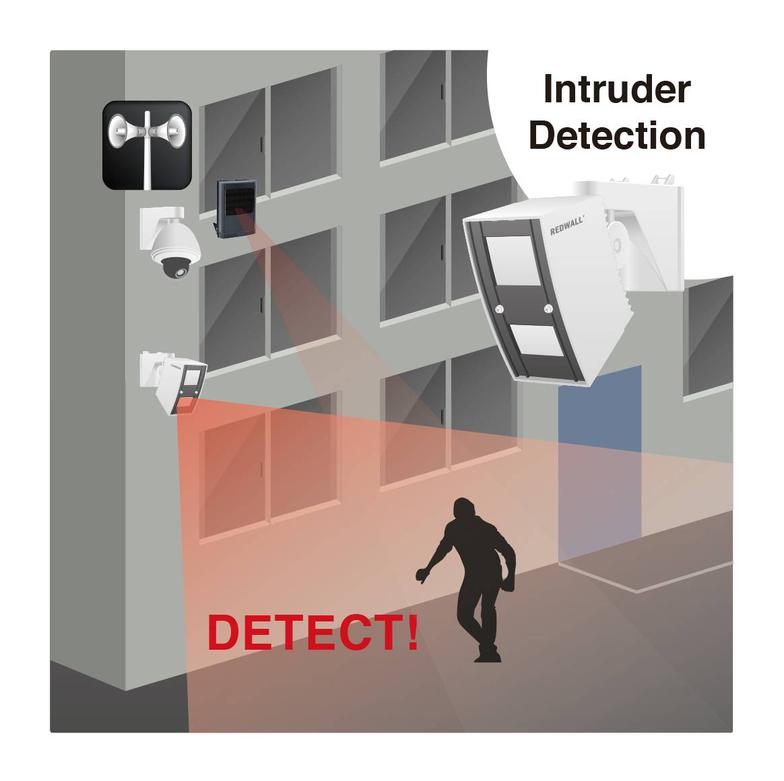
Detection is the First Step
Remotely monitored systems are event driven and rely on a trigger:
MOTION EVENT DETECTED
Immediate Security Action Requirements:
- High Frame Rate Recording
- Full power, zoned lighting
- Visual verification
- Appropriate Response
Definitive IP Sensors And Detector Product Specifications
Optex has definitive product specifications for motion detection for IP perimeter applications. This includes:
- Environmental conditions that lower the effectiveness of IP video detection and surveillance
- Varying Site Configurations
- Integrated System and Power Requirements
Multiple IP Sensor and Detection Technology
Optex's multiple IP sensor and detection technology options gives you flexibility and choice based on your application needs
Pair Video Detection Technologies Optex IP Sensors and Detectors
Pair Video Detection Technologies Optex IP Sensors and Detectors
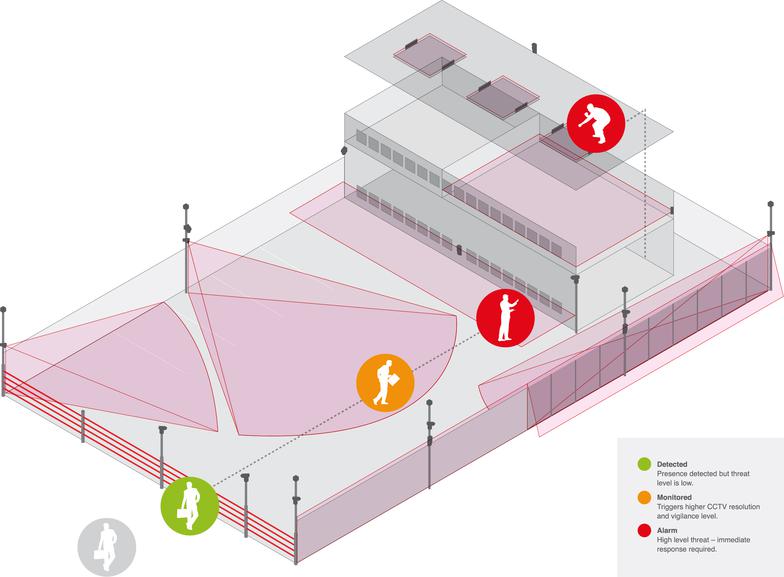
OPTEX DOUBLE KNOCK IP VIDEO SURVEILLANCE SOLUTION
Create an alarm condition when the physical detector triggers a motion event, activating camera and video analytics while reducing false alarms caused by environmental changes
“Both video analytics and thermal imaging can add an additional layer of protection to any perimeter-specific application. When used in conjunction with more traditional perimeter solutions, the degree of protection that can be realized is significant!”
Benchmark Magazine Sept 2013
Click here for corporate and product information
Contact us here